Concerned about how the NIST Cybersecurity Framework 2.0 will change your approach to cybersecurity?
The 2024 release fine-tunes its framework with a new ‘Govern’ function and updates to existing components, reflecting cutting-edge challenges and stakeholder feedback.
This article cuts through the complexity to deliver the essentials on transitioning to CSF 2.0, ensuring you are equipped for the future of cyber risks.
Key Takeaways
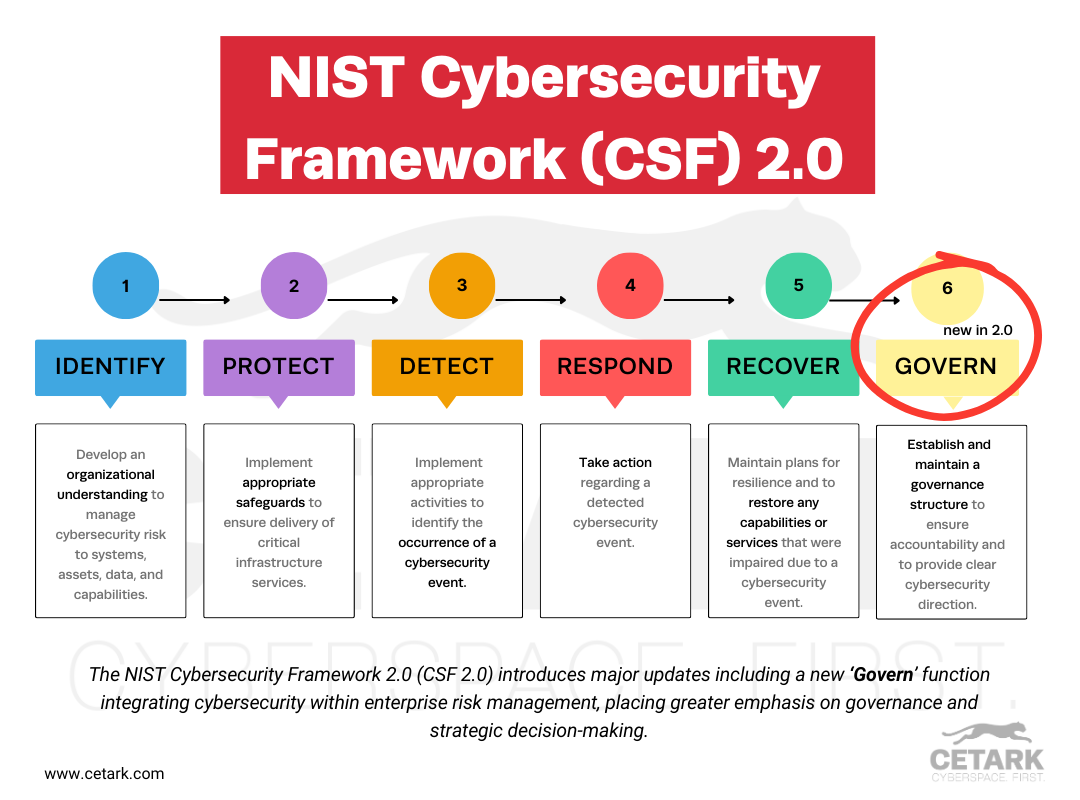
The NIST Cybersecurity Framework 2.0 (CSF 2.0) introduces major updates, including a new ‘Govern’ function that integrates cybersecurity within enterprise risk management, emphasizing governance and strategic decision-making.
CSF 2.0 has been shaped by extensive stakeholder engagement, with the development process including feedback from international workshops, public webinars, and requests for information to ensure the framework meets diverse needs and challenges.
Aligning with CSF 2.0 involves using provided resources such as the CSF 2.0 Reference Tool for implementation, conducting gap assessments, and leveraging informative references to enhance organizations’ cybersecurity risk management practices.
Unveiling the NIST Cybersecurity Framework 2.0
The NIST Cybersecurity Framework has undergone a significant transformation from its inception in response to a 2013 Presidential Executive Order. The order directed NIST to work with the private sector to establish a voluntary cybersecurity framework. The outcome of this collaboration was the first version of the NIST CSF, a framework designed to help organizations manage their cybersecurity risks.
The evolution to CSF 2.0 brought about significant updates, expanding its scope, adjusting core functions, and enhancing guidance on the use of profiles. The feedback from a broad community of stakeholders influenced these changes, showcasing NIST’s commitment to a collaborative approach. With its expected release in early 2024, CSF 2.0 aligns with the current cybersecurity landscape, providing organizations with an updated tool to tackle their cybersecurity challenges.
The Evolution from CSF 1.0 to CSF 2.0
The transition from CSF 1.0 to CSF 2.0 is not merely a cosmetic upgrade. It represents a significant evolution in the approach to cybersecurity risk management. The revised framework includes an expanded scope, adjustments to core functions, and richer guidance on the use of profiles.
This evolution has been shaped by comprehensive feedback from various stakeholders. Through public webinars, workshops, and requests for information, NIST engaged with over 3,900 attendees from more than 100 countries, ensuring transparency and collaborative evolution in the development of CSF 2.0.
The final version of CSF 2.0 is a testament to NIST’s dedication to collaborative evolution and its commitment to addressing stakeholder needs.
The Expanded Scope of CSF 2.0
CSF 2.0 broadens its reach, promising to cater to a broader swath of organizations. One major addition to the framework is the ‘Govern’ function, which aims to better integrate cybersecurity risk management with broader enterprise risk management practices. This function emphasizes informed decision-making on cybersecurity strategy, treating cybersecurity as a critical factor of enterprise risk, on par with financial and reputational risks.
Furthermore, supply chain risk management is now more prominently featured within the ‘Govern’ function, signifying its increased significance within the cybersecurity domain. CSF 2.0 highlights the necessity of managing these risks by requiring the assessment of the cybersecurity postures of suppliers as part of an organization’s cybersecurity strategy. This expanded scope, coupled with its expected translations into multiple languages and alignment with ISO/IEC standards, increases its utility for global entities.
Incorporating Stakeholder Feedback
The development of CSF 2.0 has been a collective effort, with NIST actively engaging stakeholders throughout the process. The first workshop alone saw participation from more than 3,900 attendees from over 100 countries, reflecting wide public engagement in the journey to CSF 2.0. This engagement was facilitated through public webinars, in-person and virtual workshops, and a Request for Information, ensuring a diverse range of inputs for the development of the framework.
The feedback process for CSF 2.0 included public comment on a concept paper, a discussion draft, and the draft version of CSF 2.0, enhancing the transparency of the development process. This collaborative approach has resulted in a framework that is more helpful for a broader audience, with resources based on input from written responses, working sessions, and workshop discussions.
Breaking Down the Updated Key Functions
At its core, CSF 2.0 introduces a new function to its framework, showcasing the prioritization of governance within cybersecurity risk management. Additionally, the existing functions within the framework have been refined to enhance their clarity and convey their relevance more effectively.
Governance elements, for instance, are now grouped under the newly added ‘Govern’ function. The structure of these existing functions has been updated to align better with contemporary cybersecurity challenges and the expectations of various stakeholders. The framework now provides a clear roadmap for organizations to build and enhance their cybersecurity risk management practices.
The Introduction of the “Govern” Function
Adding the ‘Govern’ function in CSF 2.0 is a breakthrough in cybersecurity risk management. This function:
- Places a greater emphasis on governance
- Elevates cybersecurity risk management concerns to the strategic level
- Acknowledges them as a critical enterprise risk factor.
Aligning with governance and regulatory requirements is a key aspect of the ‘Govern’ function, ensuring that cybersecurity priorities are set and accountability is held at the top levels of management. This function promotes executive and board-level engagement in cybersecurity practices, crucial for transparent and strategic alignment with business goals and regulatory compliance.
Refinements to Existing Functions
The existing functions of CSF 2.0 have been refined to provide clearer guidance and improve the utility of these functions for organizations. The functions are:
- Identify
- Protect
- Detect
- Respond
- Recover
The NIST Cybersecurity Framework has made several updates to its functions:
- The Protect function has been modified to provide more explicit guidance through the consolidation of categories, aiding in the prevention and mitigation of cybersecurity risks.
- The Detect function has been streamlined to prioritize the timely discovery of cybersecurity events.
- The Respond function has been streamlined to prioritize effective action post-threat detection.
- The Recover function has been streamlined to prioritize secured recovery processes.
These update aims enhance the framework’s effectiveness in addressing the most recent cybersecurity challenges.
Enhanced Utility of Profiles
Another significant update in CSF 2.0 is the enhanced guidance on profiles. The framework introduces ‘Community Profiles,’ which describe collaborative efforts within a community to develop cybersecurity risk management guidance. These profiles differentiate from ‘Organizational Profiles’ that focus internally on a single organization.
To aid communities in building effective cybersecurity management, CSF 2.0 provides a specific guide for creating and using Community Profiles. This guide details the ‘Community Profile Lifecycle’. Moreover, the profiles in CSF 2.0 allow organizations to practically understand, assess, and tailor cybersecurity outcomes with actionable suggestions and implementation examples provided by the framework.
The final version of CSF 2.0 includes Synchronized Resources and updated Implementation Examples, which aid in utilizing profiles effectively.
Aligning Your Organization with NIST CSF 2.0
 can align with CSF 2.0 by utilizing the tailored implementation resources provided by NIST. These resources include examples and quick-start guides, catering to different organizational needs, such as those of small businesses and enterprise risk managers.
can align with CSF 2.0 by utilizing the tailored implementation resources provided by NIST. These resources include examples and quick-start guides, catering to different organizational needs, such as those of small businesses and enterprise risk managers.
The adoption of CSF 2.0 is facilitated by the CSF 2.0 Reference Tool, a tool that allows organizations to navigate core guidance efficiently in user-friendly and machine-readable formats. To achieve alignment, organizations must conduct the following steps:
- Use the CSF 2.0 Reference Tool to navigate core guidance.
- Conduct gap assessments to pinpoint discrepancies between current cybersecurity practices and the recommended standards of CSF 2.0.
- Prioritize cybersecurity improvements based on the assessment results.
Moreover, enhanced communication with stakeholders is vital to facilitate the transition to and compliance with CSF 2.0, thus expediting the attainment of cybersecurity objectives.
Assessment and Gap Analysis
The alignment process begins with an assessment and gap analysis. This analysis involves comparing an organization’s current cybersecurity measures against the framework’s guidance to identify areas that need improvement or enhancement.
As part of the NIST CSF 2.0 implementation, organizations should establish current and target profiles to assess cybersecurity outcome achievement and identify areas for improvement. To streamline the implementation process, organizations can leverage the overlap with other frameworks, reducing the time and resources required for manual mapping.
Implementation Strategies for Small and Large Enterprises
CSF 2.0 provides implementation strategies for both small and large enterprises. It includes resources specifically designed to address the varied needs and cybersecurity sophistication levels of different organizations.
For small businesses, NIST provides targeted resources such as the Small Business Cybersecurity Corner website. This resource aims to make cybersecurity information accessible and actionable for small enterprises. These targeted resources help organizations of all sizes implement the framework effectively and manage their cybersecurity risks efficiently.
Leveraging Informative References
CSF 2.0 also provides a slew of informative references and tools to assist in the implementation process. The updated framework offers a searchable catalog of informative references, allowing users to map their cybersecurity actions and policies to the framework, and to cross-reference the CSF’s guidance with over 50 other cybersecurity documents.
The NIST CSF 2.0 Reference Tool facilitates the implementation of the CSF by providing a more accessible, machine-readable format, and supporting features, including exporting selected data using search terms. Further, the Cybersecurity and Privacy Reference Tool (CPRT) compiles a set of interrelated NIST guidance documents in a user-friendly format, enhancing communication of cybersecurity concepts and linking the CSF to other key resources.
NIST maintains the CSF as a living document online, with a commitment to continuous updates guided by community engagement.
The Role of NIST CSF 2.0 in Modern Cybersecurity

CSF 2.0 plays a crucial role in modern cybersecurity. It provides a taxonomy of cybersecurity outcomes applicable to a diverse range of organizations, irrespective of their size, sector, or maturity level.
The updated guidance offered by CSF 2.0 targets industry, government agencies, and various organizations, focusing on mitigating increased cybersecurity risks. While CSF 2.0 suggests a direction for cybersecurity risk management, it does not demand specific practices, instead mapping to resources for achieving the framework’s outcomes.
The framework is engineered to enhance how organizations articulate their cybersecurity risk and strategies, both internally and externally.
Addressing Recent Cybersecurity Challenges
CSF 2.0 aims to tackle evolving cybersecurity threats. It extends its applicability to encompass all organizations, transitioning beyond the confines of just critical infrastructure, which aligns with the overarching strategy at the national cybersecurity level.
The framework champions a robust approach to cybersecurity that emphasizes understanding, assessing, prioritizing, and effectively communicating cybersecurity risks across all levels of an organization. It is strategically designed to improve cyber risk communication with external partners and suppliers while incorporating these issues into the broader enterprise risk management strategies.
In preparation for the quantum computing era, NIST is actively collaborating with the cryptography community to develop encryption methods that will be resilient to the threats posed by the advent of quantum computing capabilities.
Working Closely with the National Institute of Standards and Technology
NIST’s commitment to enhancing cybersecurity is evident in its continuous refinement of frameworks like the Cybersecurity Framework and the Risk Management Framework. The institute’s dedication is further highlighted by its engagement with industry and government stakeholders through NIST’s Applied Cybersecurity Division, facilitating effective solutions to emerging cybersecurity challenges.
NIST prioritizes the principles of transparency, traceability, and openness in the creation and implementation of cybersecurity standards, promoting trust and excellence in outcomes. It employs methods such as Requests for Information and public commenting periods to encourage stakeholder participation and gather expert inputs on cybersecurity. The Information Security and Privacy Advisory Board at NIST contributes diverse perspectives from various sectors, influencing the direction of cybersecurity efforts.
Budget Considerations for Implementing NIST CSF 2.0
 CSF 2.0 requires comprehensive planning, budget allocation, and organization-wide commitment. The transition may be time-consuming, require considerable resources, and entail significant costs. Organizations must develop a measurable plan for CSF implementation, including clear budget considerations to guide the process. Implementation requires organization-wide commitment, which may introduce costs for training programs and changes in management practices.
CSF 2.0 requires comprehensive planning, budget allocation, and organization-wide commitment. The transition may be time-consuming, require considerable resources, and entail significant costs. Organizations must develop a measurable plan for CSF implementation, including clear budget considerations to guide the process. Implementation requires organization-wide commitment, which may introduce costs for training programs and changes in management practices.
Ongoing costs will be incurred for monitoring and evaluating the implementation to identify areas of improvement, pointing to a need for budgeting for continuous improvement processes. Companies with limited resources or cybersecurity know-how may consider engaging with security service providers, which is a significant budget consideration for CSF implementation. However, while initial implementation may seem costly, it is an investment that can add value to businesses and improve their competitiveness in security-focused markets.
Summary
In conclusion, CSF 2.0 stands as a robust tool to tackle the pressing cybersecurity challenges of the modern age. The framework offers a comprehensive taxonomy of cybersecurity outcomes, catering to a broad array of sectors and the needs of organizations of various sizes. By incorporating stakeholder feedback, refining key functions, and providing extensive guidance on implementation, CSF 2.0 ensures that organizations can navigate the landscape of cybersecurity risks effectively.
The journey to align with CSF 2.0 may seem daunting, given the comprehensive planning and budget considerations it requires. However, the benefits of implementing the framework far outweigh the costs. CSF 2.0 provides organizations with a clear roadmap to enhance their cybersecurity risk management practices, enabling them to build a robust defense against the ever-evolving cybersecurity threats.
Frequently Asked Questions
What is the NIST Cybersecurity Framework 2.0?
The NIST Cybersecurity Framework 2.0 is a comprehensive framework designed to help organizations manage and reduce cybersecurity risks, aligning with the National Cybersecurity Strategy and catering to organizations of different sizes and sectors.
What are the key functions of CSF 2.0?
The key functions of CSF 2.0 are to Identify, Protect, Detect, Respond, Recover, and Govern, providing a roadmap for organizations to enhance their cybersecurity risk management practices.
How can organizations align with CSF 2.0?
Organizations can align with CSF 2.0 by utilizing tailored implementation resources, conducting gap assessments, and enhancing communication with stakeholders. These steps are essential for successful alignment with CSF 2.0.
What are the budget considerations for implementing CSF 2.0?
To implement CSF 2.0, organizations need to budget for training programs, changes in management practices, and ongoing monitoring and evaluation to ensure successful implementation.
How does NIST CSF 2.0 address recent cybersecurity challenges?
NIST CSF 2.0 addresses recent cybersecurity challenges by providing a taxonomy of cybersecurity outcomes, refining key functions, and incorporating stakeholder feedback, emphasizing understanding, assessing, prioritizing, and effectively communicating cybersecurity risks across all levels of an organization.