Enhancing the security of industrial control systems (ICS) is critical, and executing network segmentation and isolation stands as a fundamental strategy. This guide cuts through the complexity to directly address
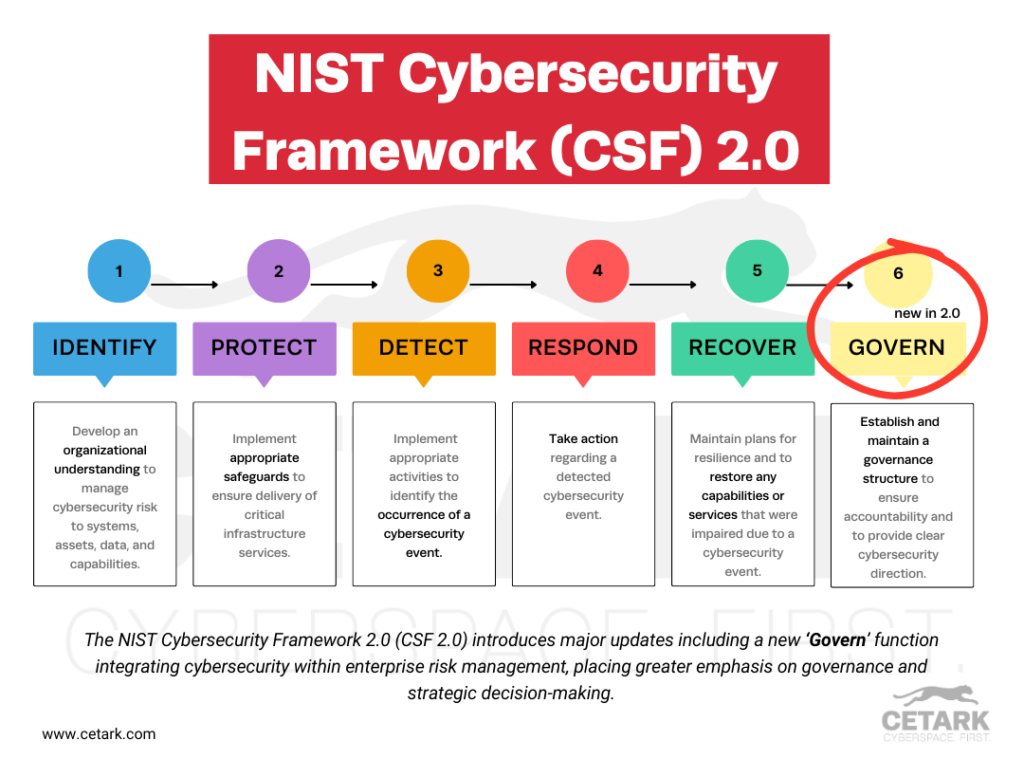
ContinueConcerned about how the NIST Cybersecurity Framework 2.0 will change your approach to cybersecurity? The 2024 release fine-tunes its framework with a new ‘Govern’ function and updates to existing components,
ContinueHow do AI and machine learning redefine the role of AI and machine learning in enhancing Continuous Threat Exposure Management (CTEM)? By equipping cybersecurity teams with tools for faster threat
ContinueWhat exactly is phishing, and how can you recognize and prevent it? Our Phishing 101 guide cuts through the complexity to deliver straightforward insights into identifying phishing attempts and safeguarding
ContinueBackground The Department of Health and Human Services (HHS) aids the Healthcare and Public Health (HPH) sector in preparing for and responding to cyber threats. HHS, in collaboration with the
Continue