When data is stolen in a breach, it embarks on a journey through the criminal underworld. From breaches to dark web sales, the lifecycle of stolen data from data breach
ContinueThe 2024 Space Threat Assessment, published by the Center for Strategic and International Studies (CSIS), highlights a worrying trend: increased counterspace capabilities among nations like China, Russia, and others. These counterspace
ContinueEnhancing the security of industrial control systems (ICS) is critical, and executing network segmentation and isolation stands as a fundamental strategy. This guide cuts through the complexity to directly address
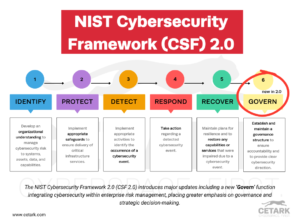
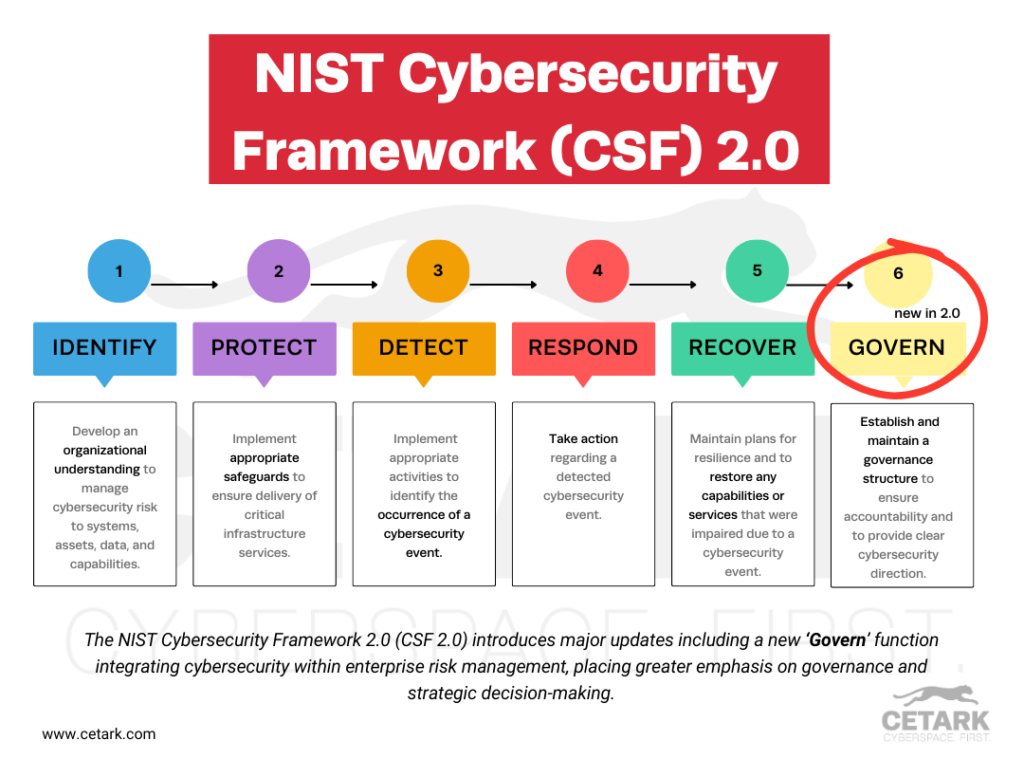
ContinueConcerned about how the NIST Cybersecurity Framework 2.0 will change your approach to cybersecurity? The 2024 release fine-tunes its framework with a new ‘Govern’ function and updates to existing components,
ContinueHow do AI and machine learning redefine the role of AI and machine learning in enhancing Continuous Threat Exposure Management (CTEM)? By equipping cybersecurity teams with tools for faster threat
Continue